Intune Settings Rundown - 2408

Continuing my new (semi) regular feature to document interesting new or updated Intune policy settings and UI changes in an easily digestible format!
Note: UI changes can sometimes take time so may not be visible immediately in your tenant.
Windows Hello for Business
Last month introduced brand new WHfB policies under Endpoint Security > Account Protection. This was one of the last "legacy" policy types to be converted so was a welcome change, but many people were confused with what "Passport for Work" is.
Thankfully the template has been updated to not only update that wording to be reflective of the feature, and be clearer around settings that are Device or User scoped:
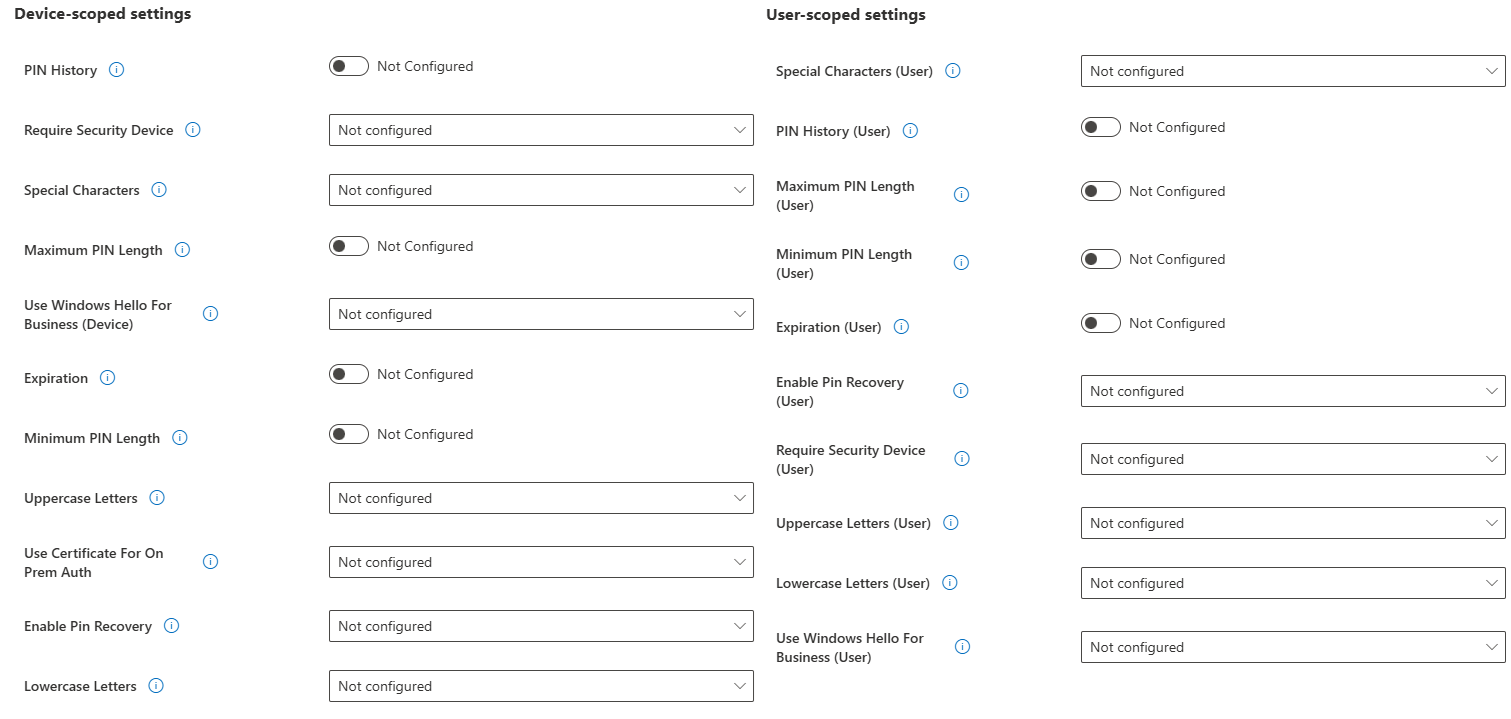
Still hoping to see Cloud Kerberos Trust option made available in the future.
Fun Fact: The old preview version of this dynamically applied Device or User scope settings depending on what you assigned it to! Now you've got to think about it 😄
MacOS DDM
It's an absolute Mac bonanza this month, with a bunch of new DDM (Declarative Device Management) settings being added.
NOTE: These are all settings from the Apple Beta DDM so are only applicable to MacOS 15 Sequoia.
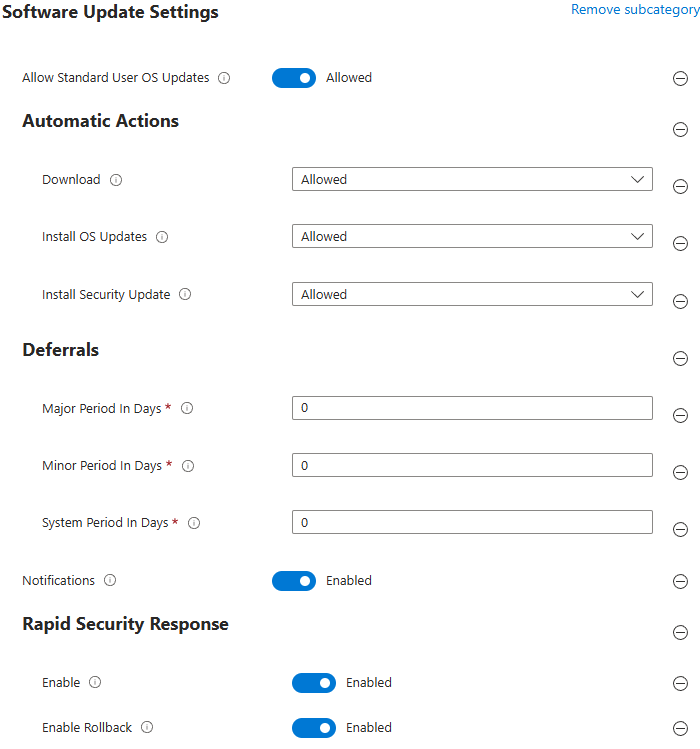
Software Update Settings
Some really neat new Software Update configuration
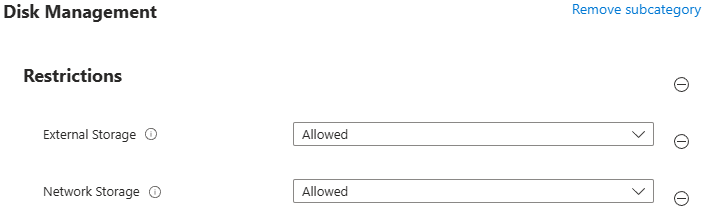
Disk Management Settings
Settings to restrict the use of External or Network Storage. Available options are the same for both, but the tooltip for External shows the following options:
- Allowed - external storage that is read-write or read-only will be mounted.
- ReadOnly - only external storage that is read-only will be automatically mounted. Note that external storage that is read-write will not be mounted read-only.
- Disallowed - no external storage will be mounted.
Safari Extension Settings
You can also now allow/deny extensions within Safari, even though you'll obviously be using Edge ;)

Microsoft Office
Just the one Office setting, but a welcome one, restricting the ability for potential data exfiltration by copying or moving items to non-authorised accounts.
L_PreventCopyingOrMovingItemsBetweenAccounts
| Policy Name | Prevent copying or moving items between accounts |
| Policy Location | Microsoft Outlook 2016\\Account Settings\\Exchange |
| Policy Tooltip | This policy setting allows you to prevent items from being copied or moved to other accounts or PSTs. If you enable this policy setting, items will be prevented from being moved or copied to other accounts or PSTs. Enter one of the following details: "Contoso.com": prevents copying or moving from the account corresponding to the listed domain "*": prevents copying from all accounts and PST's "SharePoint": prevents copies or moves from the SharePoint PST If you disable or do not configure this policy setting, copying or moving items between accounts or PSTs is allowed. |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (User) |
Windows 365/Remote Desktop
More new controls for Windows 365 and Remote Desktop, this time focused on disconnection of the session when the device locks.
The CSP docs currently show these as only applicable to Windows Insider versions but the tooltips do not.
TS_DISCONNECT_ON_LOCK_POLICY
| Policy Name | Disconnect remote session on lock for legacy authentication |
| Policy Location | Administrative Templates\\Windows Components\\Remote Desktop Services\\Remote Desktop Session Host\\Security |
| Policy Tooltip | This policy setting allows you to configure the user experience when the Remote Desktop session is locked by the user or by a policy. You can specify whether the remote session will show the remote lock screen or disconnect when the remote session is locked. Disconnecting the remote session ensures that a remote session cannot be left on the lock screen and cannot reconnect automatically due to loss of network connectivity. This policy applies only when using legacy authentication to authenticate to the remote PC. Legacy authentication is limited to username and password, or certificates like smartcards. Legacy authentication doesn't leverage the Microsoft identity platform, such as Microsoft Entra ID. Legacy authentication includes the NTLM, CredSSP, RDSTLS, TLS, and RDP basic authentication protocols. If you enable this policy setting, Remote Desktop connections using legacy authentication will disconnect the remote session when the remote session is locked. Users can reconnect when they're ready and re-enter their credentials when prompted. If you disable or do not configure this policy setting, Remote Desktop connections using legacy authentication will show the remote lock screen when the remote session is locked. Users can unlock the remote session using their username and password, or certificates. |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (Device) |
TS_DISCONNECT_ON_LOCK_AAD_POLICY
| Policy Name | Disconnect remote session on lock for Microsoft identity platform authentication |
| Policy Location | Administrative Templates\\Windows Components\\Remote Desktop Services\\Remote Desktop Session Host\\Security |
| Policy Tooltip | This policy setting allows you to configure the user experience when the Remote Desktop session is locked by the user or by a policy. You can specify whether the remote session will show the remote lock screen or disconnect when the remote session is locked. Disconnecting the remote session ensures that a remote session cannot be left on the lock screen and cannot reconnect automatically due to loss of network connectivity. This policy applies only when using an identity provider that uses the Microsoft identity platform, such as Microsoft Entra ID, to authenticate to the remote PC. This policy doesn't apply when using Legacy authentication which includes the NTLM, CredSSP, RDSTLS, TLS, and RDP basic authentication protocols. If you enable or do not configure this policy setting, Remote Desktop connections using the Microsoft identity platform will disconnect the remote session when the remote session is locked. Users can reconnect when they're ready and can use passwordless authentication if configured. If you disable this policy setting, Remote Desktop connections using the Microsoft identity platform will show the remote lock screen when the remote session is locked. Users can unlock the remote session using their username and password, or certificates. |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (Device) |
Massive thanks to Tom Plant in making these blogs far easier for me to write up!😊
And as always, thanks for reading!



