Intune Settings Rundown - 2407

Continuing my new (semi) regular feature to document interesting new or updated Intune policy settings and UI changes in an easily digestible format!
Note: UI changes can sometimes take time so may not be visible immediately in your tenant.
Windows Hello for Business
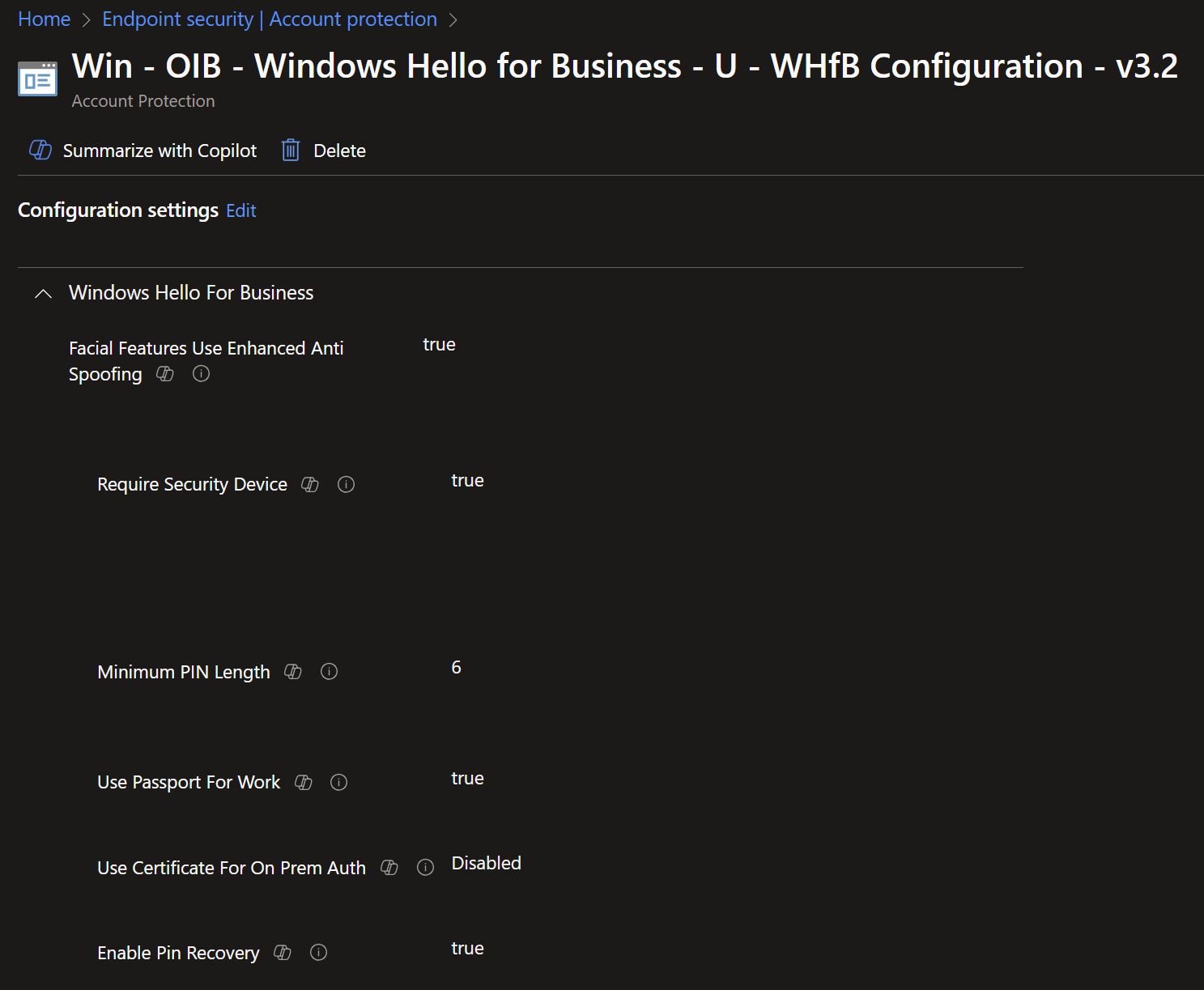
Windows Hello for Business policies via the Account Protection page in Endpoint Security have been in Preview for... A while. They've finally been updated to be Settings Catalog-backed!
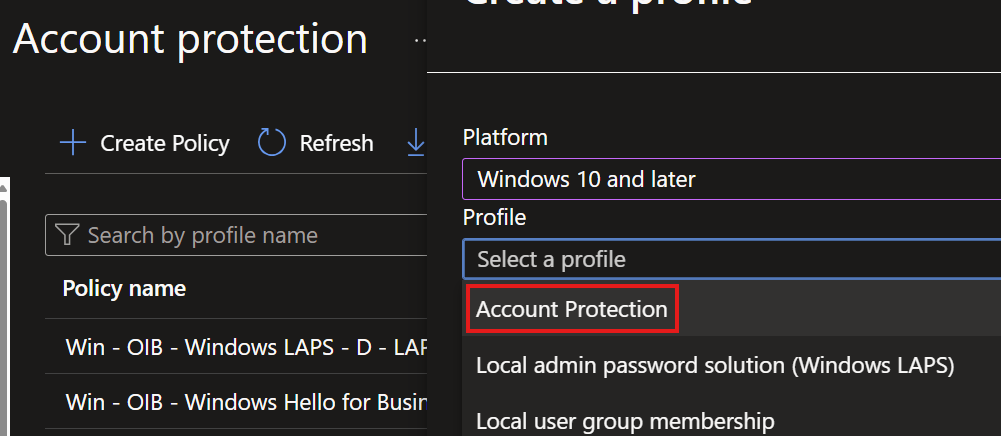
The new policy type has different sections depending on whether you're wanting to apply the policy to Users or Devices, however I have noticed that some WHfB configuration available via the old template (namely "Allow biometric authentication") is currently missing. It would also be nice to have the Cloud Kerberos Trust option available in the template as it's what everyone should use if possible.
Microsoft Edge
Some new policies added for Edge v126:
InternetExplorerSetForegroundWhenActive
| Policy Name | Keep the active Microsoft Edge window with an Internet Explorer mode tab always in the foreground. |
| Policy Location | Microsoft Edge |
| Policy Tooltip | This policy controls whether to always keep the active Microsoft Edge window with an Internet Explorer mode tab in the foreground. If you enable this policy, the active Microsoft Edge window with an Internet Explorer mode tab will always be in the foreground. If you disable or don't configure this policy, the active Microsoft Edge window with an Internet Explorer mode tab will not be kept in the foreground. To learn more about Internet Explorer mode, see https://go.microsoft.com/fwlink/?linkid=2094210 |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (Device) and (User) |
ProactiveAuthWorkflowEnabled
| Policy Name | Enable proactive authentication |
| Policy Location | Microsoft Edge |
| Policy Tooltip | This policy controls the proactive authentication in Microsoft Edge, that connects the signed-in user identity with Microsoft Bing, MSN and Copilot services for a smooth and consistent sign-in experience. If you enable or don't configure this policy, Microsoft Edge authentication requests are automatically sent to the services using the account that is signed-in to the browser. If you disable this policy, Microsoft Edge does not send authentications requests to these services and users will need to manually sign-in. |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (Device) and (User) |
QRCodeGeneratorEnabled
| Policy Name | Enable QR Code Generator |
| Policy Location | Microsoft Edge |
| Policy Tooltip | This policy enables the QR Code generator feature in Microsoft Edge. If you enable this policy or don't configure it, the QR Code Generator feature is enabled. If you disable this policy, the QR Code Generator feature is disabled. |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (Device) and (User) |
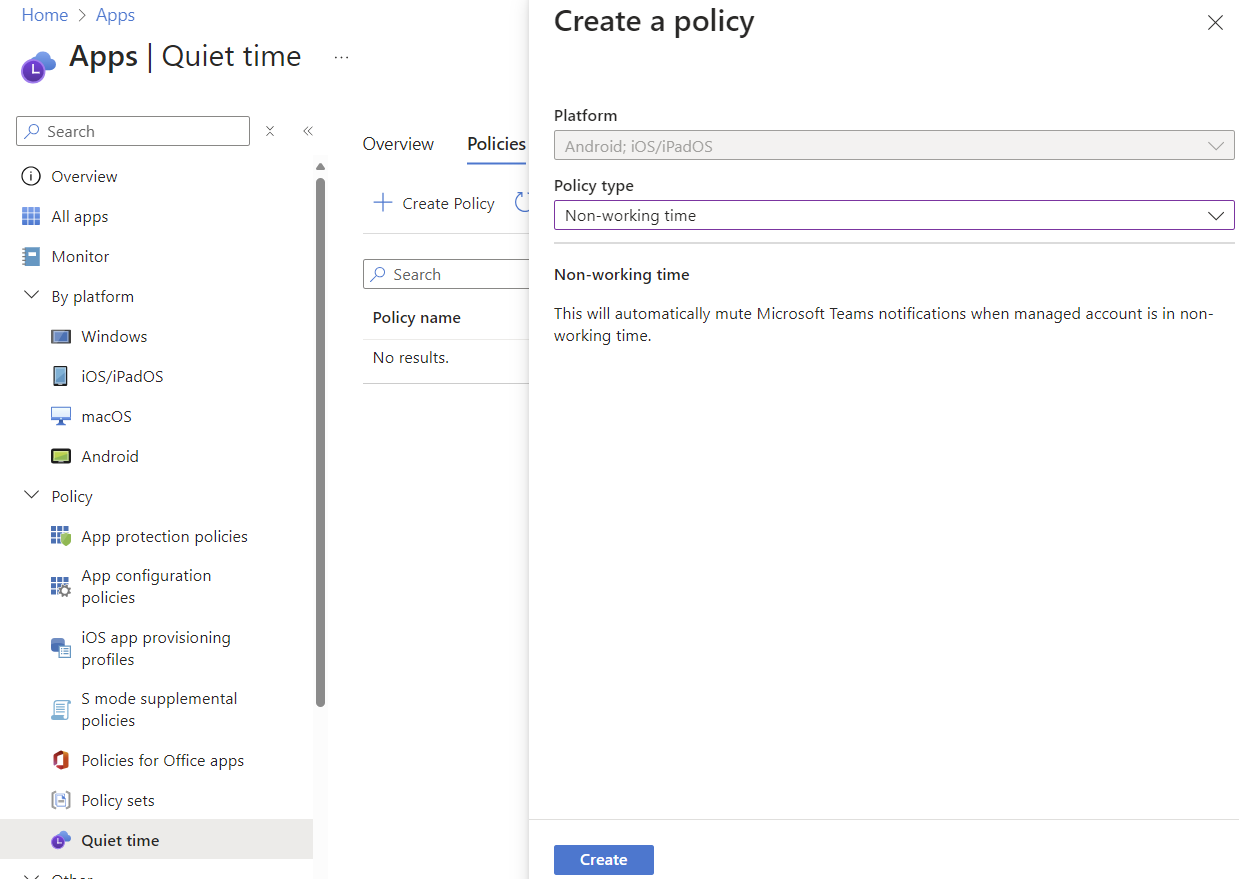
New Quiet Time Policy
A feature I think many people miss is the ability to create org-wide "Quiet Time" policies to mute Outlook and Teams notifications on Android and iOS. These have previously been available as either a specific date range, or chosen days of the week.
A new policy option is now available to adhere to a specific users working hours as defined in Outlook/Exchange and mute Teams notifications during "non-working time". Very cool addition!
Microsoft Office
AI Training and New Outlook client migration controls!
DisableTrainingMachine
| Policy Name | Disable Training of all features on the computer |
| Policy Location | Microsoft Office 2016\\Miscellaneous |
| Policy Tooltip | This policy setting allows you to disable Training of all features on the computer. If you enable this policy setting, Training of all features will be disabled on the computer. If you disable this policy setting, Training of all features is enabled on the computer. If you do not configure this policy setting, Training of all features is determined based on user policy settings. |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (Device) and (User) |
L_DisableComToWebAddinUpgrade
| Policy Name | Disable web add-in installation on migration to new Outlook for Windows (User) |
| Policy Location | Microsoft Outlook 2016\\Outlook Options\\Other |
| Policy Tooltip | This policy setting allows you to disable installation of web add-in equivalents of COM add-ins on the switch to new Outlook. The add-ins available for migration are listed in https://aka.ms/newoutlooksettings. Learn more about Outlook web add-ins at https://learn.microsoft.com/office/dev/add-ins/outlook/outlook-add-ins-overview. COM add-ins do not work in new Outlook for Windows. By default, users in the organization will get the option to install available web add-ins, in place of COM add-ins, when they move from classic Outlook for Windows. If you enable this policy setting, users will not get the option to install web add-ins in place of their COM add-ins. If you disable or do not configure this policy setting, users will get an option to install web add-ins in place of their COM add-ins. |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (User) Only |
L_DoNewOutlookAutoMigration
| Policy Name | Admin-Controlled Migration to New Outlook (User) |
| Policy Location | Microsoft Outlook 2016\\Outlook Options\\Other |
| Policy Tooltip | This policy controls the ability of IT admins to initiate the migration of users from classic Outlook to new Outlook. If you enable this policy setting, IT admins will start the process to switch users from classic Outlook to new Outlook. nIf you disable this policy setting, the migration process to new Outlook will be stopped, keeping users on their current version of Outlook without transitioning to new Outlook. If you do not set this policy setting, the migration process to new Outlook will not start, and users that have not migrated will remain on classic Outlook. Note: IT admins can also define intervals for re-initiating the migration process for users who revert to classic Outlook from new Outlook. This is managed through the NewOutlookAutoMigrationRetryIntervals policy, offering a tailored strategy for transitioning users based on organizational requirements and user feedback. |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (User) Only |
L_NewOutlookAutoMigrationRetryIntervals
| Policy Name | Number of days "New Outlook auto migration" should be paused after user untoggling back to Outlook Desktop (User) |
| Policy Location | Microsoft Outlook 2016\\Outlook Options\\Other |
| Policy Tooltip | This policy setting controls the number of days "New Outlook auto migration" should be paused after user untoggling back to Outlook Desktop. If you don't set this or set this to -1, Outlook Desktop will stop executing "New Outlook auto migration" after user untoggling back to Outlook Desktop. If you set this to 0, Outlook Desktop will execute "New Outlook auto migration" in the next boot. If you set this to N (non-zero positive) value, Outlook Desktop will pause for N days before executing "New Outlook auto migration" again after user untoggling back to Outlook Desktop. Note: This policy only applies to subscription-based Microsoft 365 Apps. |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (User) Only |
Windows 365/Remote Desktop
Brand new controls for Windows 365 and Remote Desktop to granularly restrict what a user can copy/paste either from client to server or vice-versa.
These settings are currently marked as only applicable to Windows Insider builds:
📢 Update 26/07/24: That was quick, they've already updated them and they're not just for Insider builds. They are however valid for Windows 11 only according to the CSP docs.
TS_CLIENT_CLIPBOARDRESTRICTION_CS
| Policy Name | Restrict clipboard transfer from client to server |
| Policy Location | Administrative Templates\\Windows Components\\Remote Desktop Services\\Remote Desktop Session Host\\Device and Resource Redirection |
| Policy Tooltip | This policy setting allows you to restrict clipboard data transfers from client to server. If you enable this policy setting, you must choose from the following behaviors:
* Disable clipboard transfers from client to server. * Allow plain text copying from client to server. * Allow plain text and images copying from client to server. * Allow plain text, images and Rich Text Format copying from client to server. * Allow plain text, images, Rich Text Format and HTML copying from client to server. If you disable or do not configure this policy setting, users can copy arbitrary contents from client to server if clipboard redirection is enabled. Note: This policy setting appears in both Computer Configuration and User Configuration. If both policy settings are configured, the stricter restriction will be used. |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (Device) or (User) |
TS_CLIENT_CLIPBOARDRESTRICTION_SC
| Policy Name | Restrict clipboard transfer from server to client |
| Policy Location | Administrative Templates\\Windows Components\\Remote Desktop Services\\Remote Desktop Session Host\\Device and Resource Redirection |
| Policy Tooltip | This policy setting allows you to restrict clipboard data transfers from server to client. If you enable this policy setting, you must choose from the following behaviors:
* Disable clipboard transfers from server to client. * Allow plain text copying from server to client. * Allow plain text and images copying from server to client. * Allow plain text, images and Rich Text Format copying from server to client. * Allow plain text, images, Rich Text Format and HTML copying from server to client. If you disable or do not configure this policy setting, users can copy arbitrary contents from server to client if clipboard redirection is enabled. Note: This policy setting appears in both Computer Configuration and User Configuration. If both policy settings are configured, the stricter restriction will be used. |
| Available Settings | Enabled / Disabled |
| Policy Scopes | (Device) or (User) |
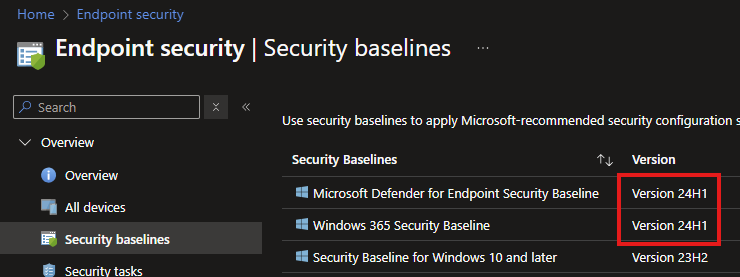
Updated Security Baselines
While I'm not a fan of the built-in Security Baselines, the Windows 365 and Defender for Endpoint baselines have been updated to version 24H1 .
Massive thanks to Tom Plant in making these blogs far easier for me to write up!😊
And as always, thanks for reading!



