From Criticism to Confidence: Windows Recall

Windows Recall gives a user the ability to go back in time by snapshotting your activity and providing a scrollable and searchable timeline to find it again.
Remember you saw a great article on ASR rules on a site that had a blue background? Search for exactly that!
As someone who's neurodivergent and has a brain that struggles with that on a regular basis, the accessibility benefits of such a tool are incredible, but I'll save some of that for another blog.
This (quite rightly) comes with some security concerns in an Enterprise environment. So what do you need to be aware of? How can you reduce risk while still providing the benefits to your users? What does the user experience look like?
Let's dig in, shall we?
I Recall Some Initial Issues...
It's fair to say that Windows Recall had a rocky start after the (IMO awful and obviously marketing-led) announcement back at Build 2024 alongside the new Copilot+ PC's.
Following the justified backlash there was a relatively quick back-pedal, followed by a full rethink of how the feature works, as well as how it's secured.
The result has been a true security-first revisit of it, brand new Enterprise controls, and an increasingly rare off-by-default approach.
Let me just summarise some (very important) highlights of the feature:
Source
Source
Source
Source
The below article goes into far more detail, and if you're both interested in the feature and security like I am, I'd highly recommend checking it out:

Mythbusters
I've already seen (and snapped at) a number of people trying to push some of those new policies to explicitly disable Recall.
These people have clearly not even done a bare minimum of reading on the feature, and are unsurprisingly now complaining that the policies are failing to apply.
Some of this is as up until now, availability has been limited to Insider builds of Windows, so while the policies are "applicable" to 24H2, they will show as failures on a non-Insider build... Which nobody should be running in an Enterprise environment as their daily driver, and in fact many security frameworks actively forbid.
HOWEVER...
Because this one's got me genuinely triggered, let me summarise this as concisely as I can:
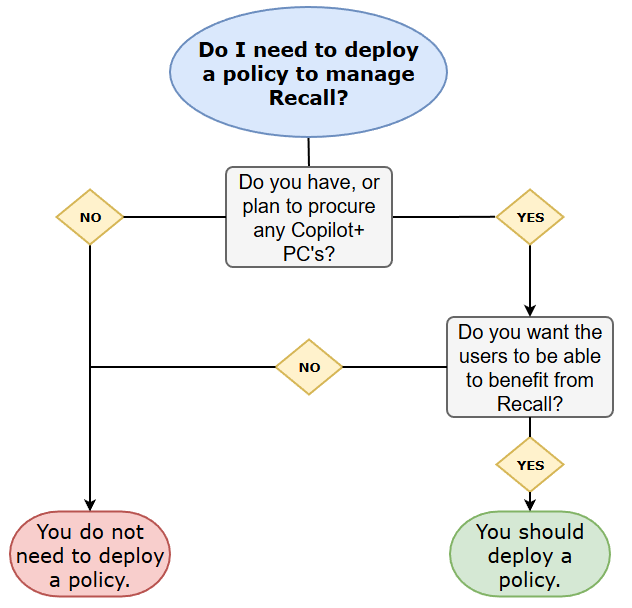
If you're knee-jerking into deploying a policy and you haven't done the necessary reading to understand that you don't need to do that, go have a word with yourself.
If you're being told to do so by management, send them my way and I'll tell them they're idiots for free :)
But, if you're an enlightened admin and curious about how to allow your users to benefit from this functionality on supported devices, then let's dive deeper...
Available Admin Controls
The available admin controls for Recall sit within the WindowsAI section of Policy CSP and as of writing this, there are a few things (ClickToDo, Cocreator & GenerativeFill) that are still missing out of the Settings Catalog. However, there's enough to get us started, and, for demonstration purposes I'll show you what I went with:
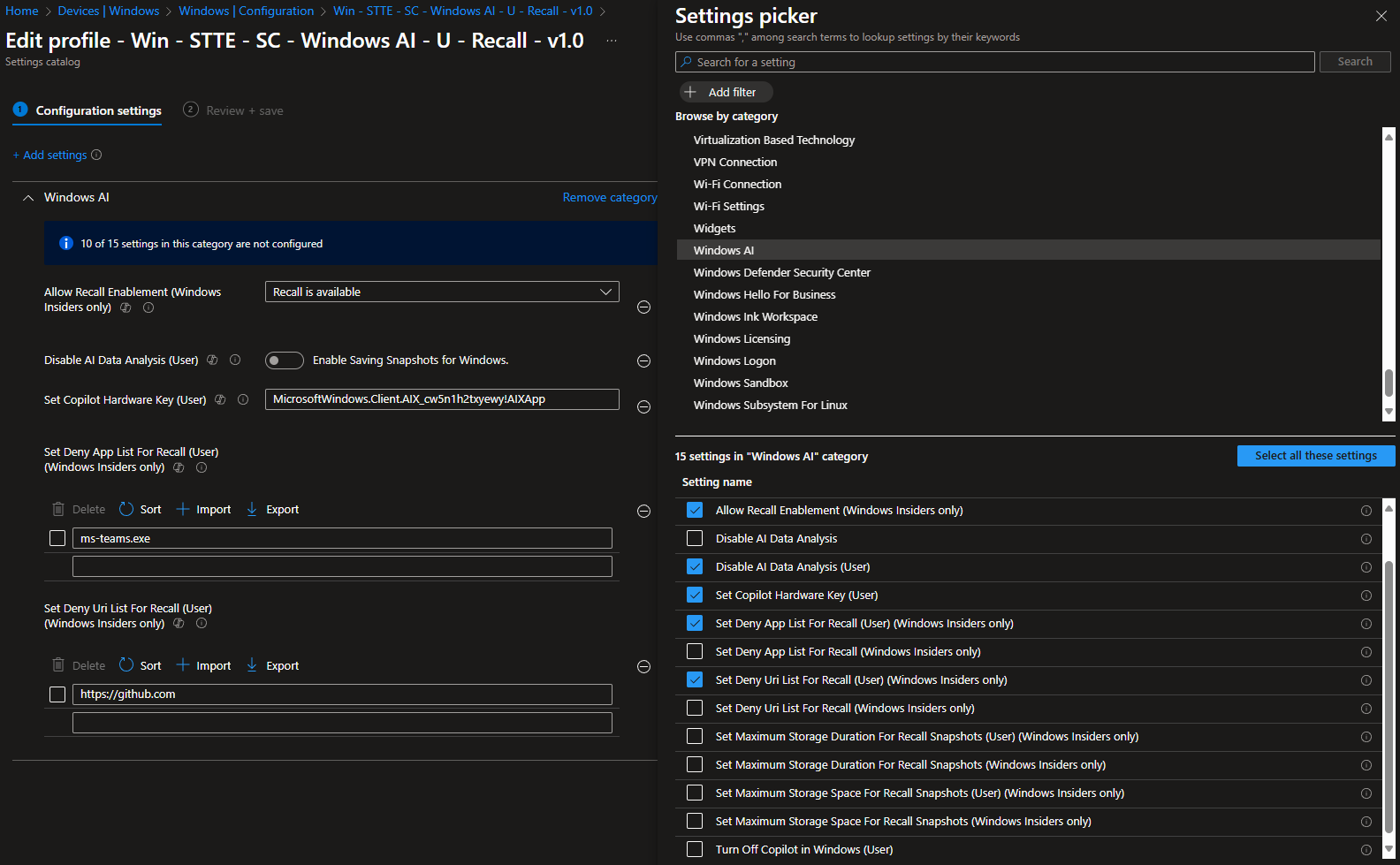
Let's just go over what I've configured here:
Allow Recall Enablement
Our primary policy. If this doesn't exist at all, a user cannot enable Recall. End of story. However, the device may still have some of the Recall components on the device in a disabled state.
Because as I want to use it, I've set this to "Recall is available".
Disable AI Data Analysis
The second important part is to enable the saving of snapshots. It's worth reiterating the following bit of the documentation:
IT administrators can't, on their own, enable saving snapshots on behalf of their users. The choice to enable saving snapshots requires individual user opt-in consent.
Simply enabling this will not enable it for the user. They still have to go do it themselves.
Because I want to enable snapshots, this is set to "Enable Saving Snapshots for Windows".
Set Copilot Hardware Key
This one is purely me wanting to make the new Copilot key on the keyboard more useful for my Recall testing, so I've set it to launch the Recall app when pressed.
Set Deny App List For Recall
This is where it gets important. As an Administrator, I can choose to block specific apps via AUMID or EXE name to stop Recall from snapshotting these.
This could be things like Teams in my demo, VS Code, or internal LOB apps.
There are some RDP clients filtered automatically, and from my testing this also includes the Windows app when connecting to W365 machines.
Set Deny Uri List For Recall
And finally, specific URL's to block from snapshots. For the demo, I've chosen to block anything from GitHub being grabbed. It's worth noting that would block any subdomains too.
These website filters are active on supported browsers, so hopefully your org isn't allowing users to install and use any old browser, or are totally blocking anything other than Edge via the Edge Management Service.
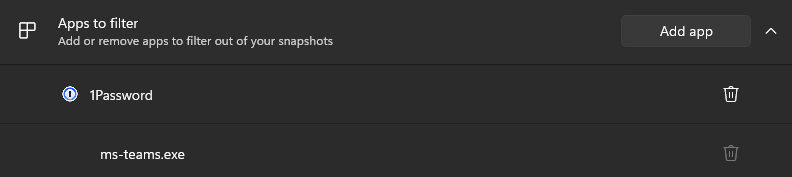
One last thing to call out is that these are purely the Admin-driven blocks. As a user, I can go and add my own to the filter list at any time, for example if I wanted to do some personal online banking that I didn't want to have snapshots generated against, I can add my bank's website to the filter list. I can't remove blocks set by policy.
The example below shows that I added 1Password to my personal filtered apps list:
User Setup & Experience
So what does the subsequent user experience feel like?
For reference, the following testing was conducted on a Surface Pro 11 with a Snapdragon X Elite, 32Gb RAM and a 1Tb SSD on the Beta Windows Insider Channel.
From a user's perspective, once the admin controls had been applied, Recall was enabled and I was able to open the Recall app which directed me into the Settings menu to enable saving snapshots:
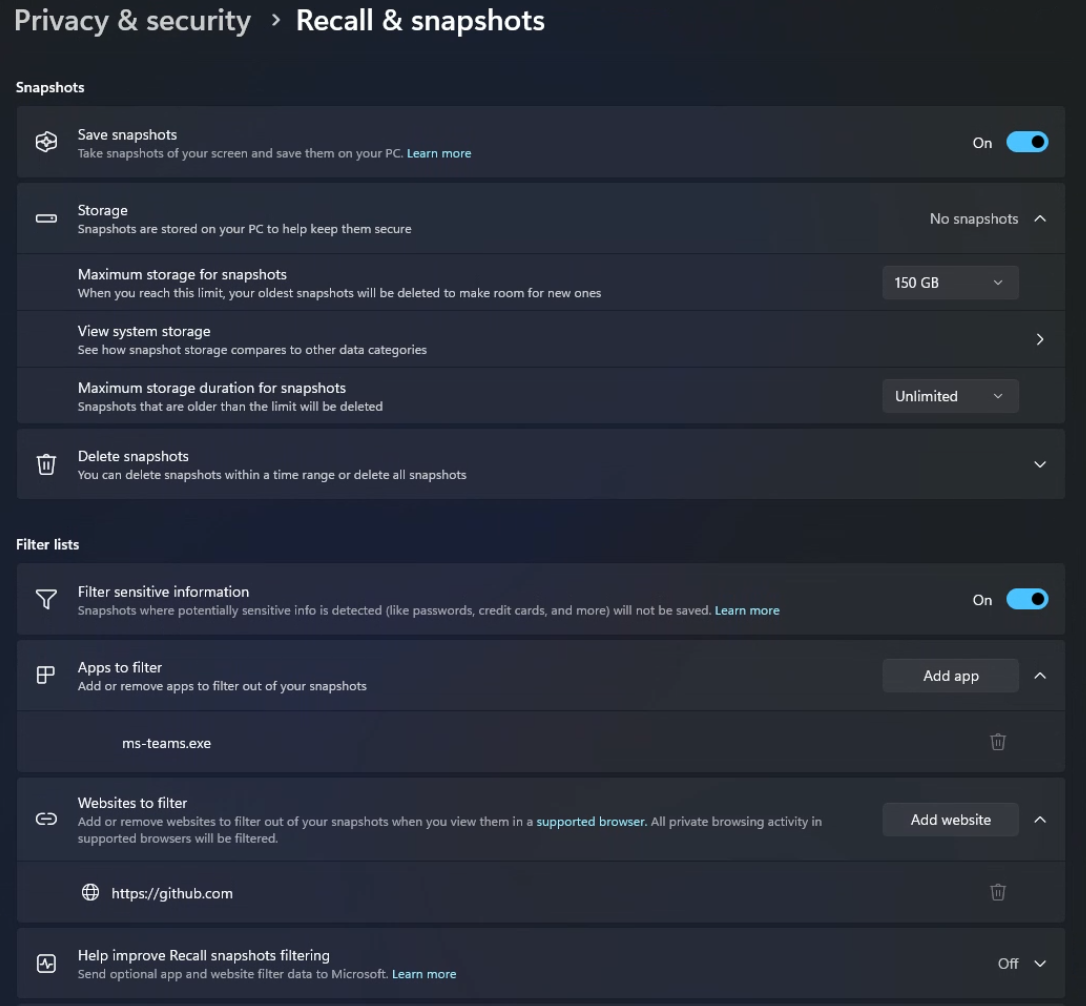
This then triggered the installation of some local AI model components:
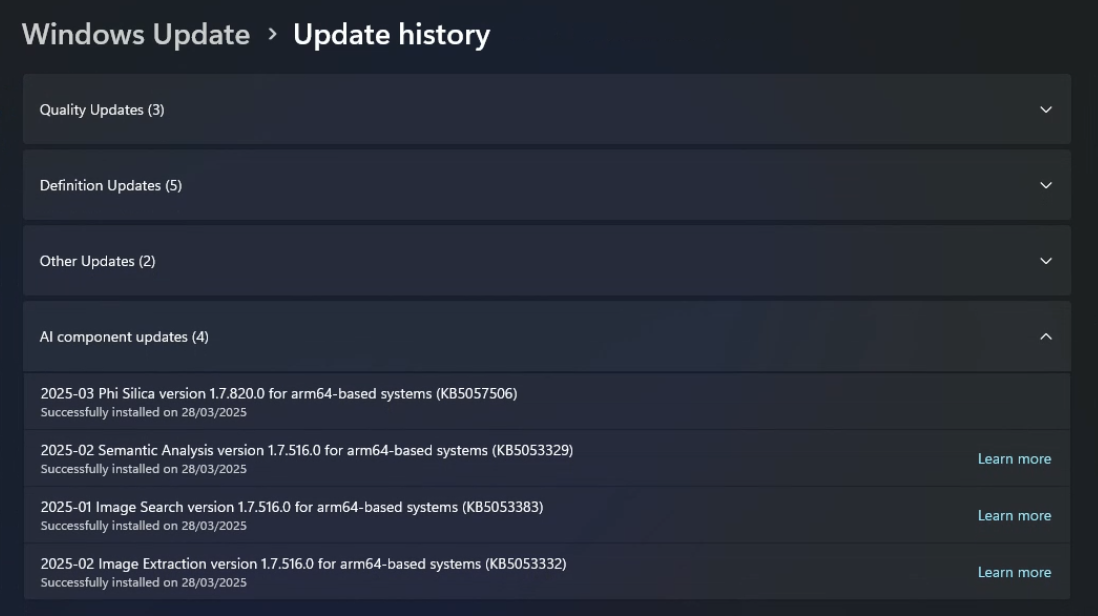
Once those were downloaded, it was just a matter of using my device for a bit until some snapshots had been generated:
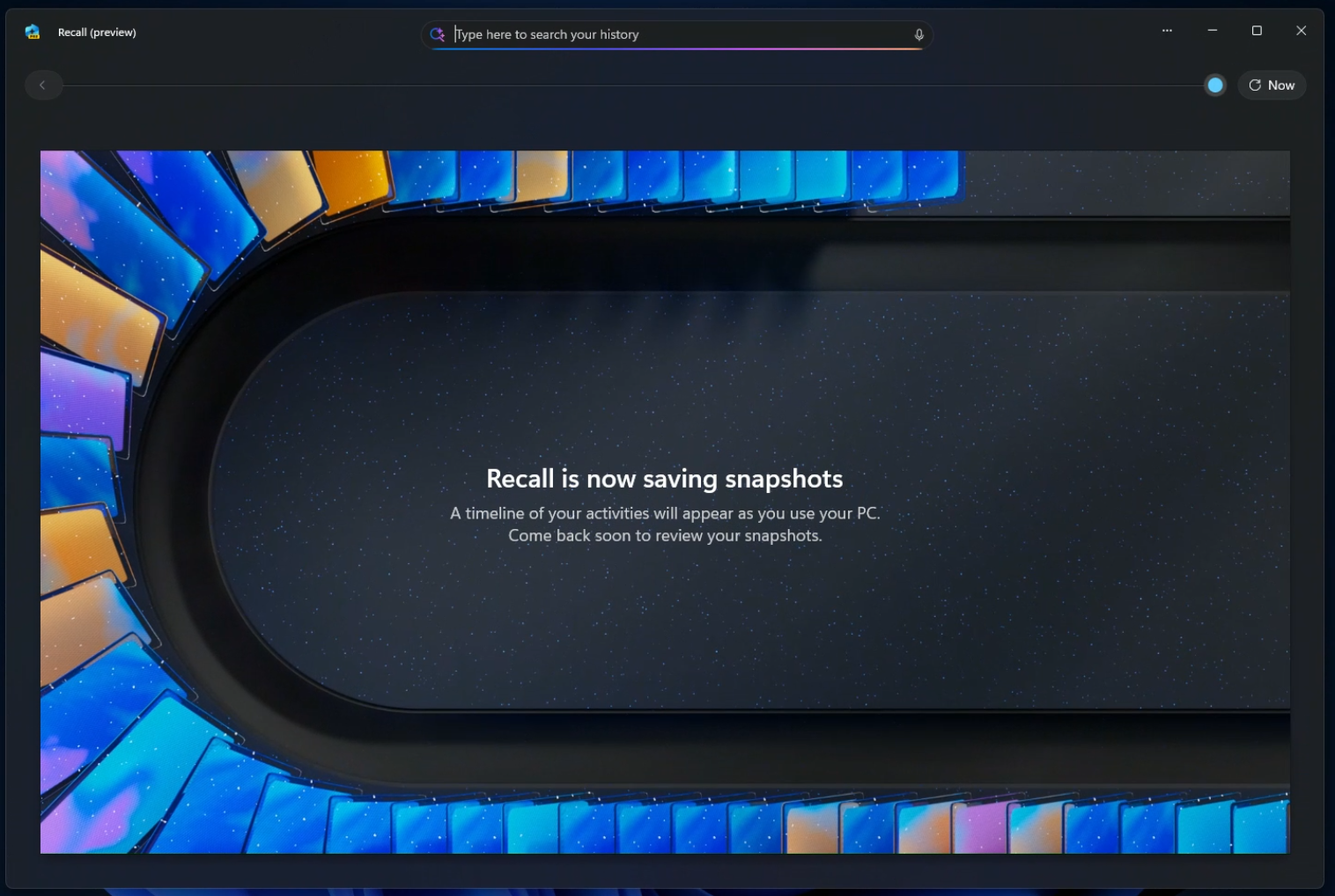
And once it had, I can use the Recall app to either scrub through a timeline of everything that's been captured, or use the search bar to find something. I can interact with the text, copy links etc. directly within the app and get back to where I wanted to be.
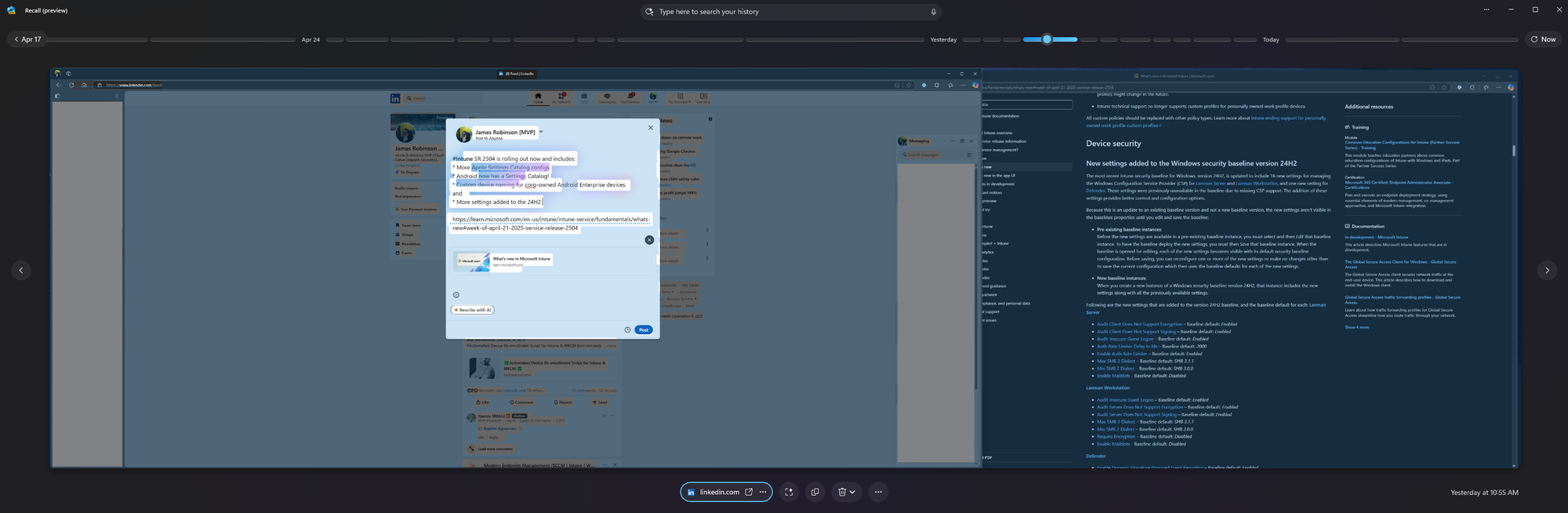
Points of Note
- As you can see from the screenshot above, it's somewhat clunky with a monitor as wide as mine, and you can only interact with the active window, even though it can see that Learn page in the background. You can't cheat the system though, un-focusing a filtered app acts like it doesn't exist at all and will capture my whole screen but just show my desktop background where the app used to be. Neat!
- While playing around with plugging my Surface into my WfH setup, I enabled the following option to see if I could use my Logitech Brio 4K (which otherwise works as a WHfB-capable facial unlock camera) with Recall.
Apart from needing to have local admin rights to do so, it did not pan out well...
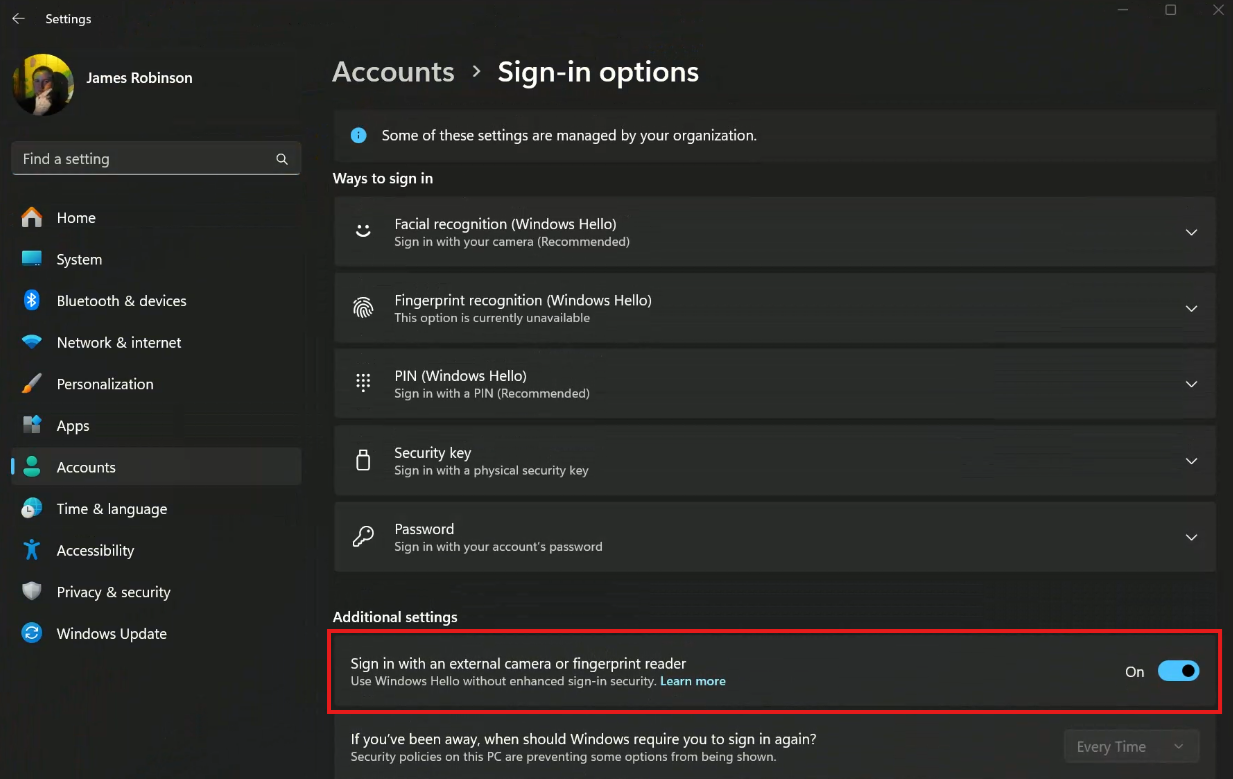
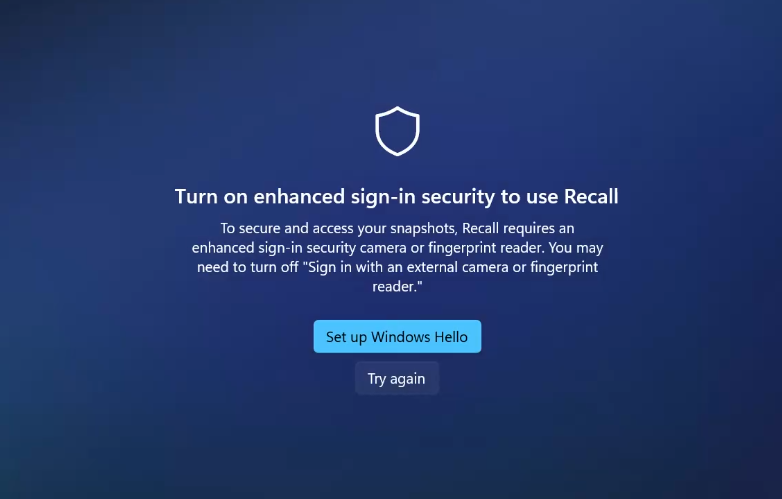
Turns out that Enhanced Sign-in Security really is a hard requirement, and I can only use the built-in Surface camera, which I'm cool with, but it was interesting to see it totally shut me down and make my stuff inaccessible until I fixed it, which actually took me to completely re-do my WHfB facial recognition setup again once I'd turned that setting off again.
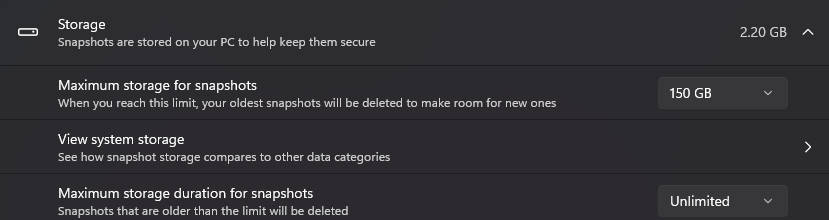
- I was pleasantly surprised by the disk space used. Over the course of a month, using my Surface daily, it's only used 2.2Gb of a max of 150Gb set. With an unlimited storage duration this means I could theoretically go back YEARS before filling the quota!
- I'd really like to see an additional admin control to override and force-enable the "Filter Sensitive Information" toggle. While it is on by default, as a user I can still go turn it off, which feels counter-productive.
This doesn't stop an admin from defining apps and/or websites to filter!
Summary
Recall is a super neat feature which demonstrates the potential power of devices with NPU's in being able to find something you saw but couldn't remember the details of where, as well as interact with that content in meaningful ways.
That said, Microsoft really hurt themselves by not developing this feature how it exists now to begin with. As it's now coming into General Availability, I can't count the number of negative news articles that are still being created about it, and it's an unpleasant truth that misinformation is 10 times harder to counter than the truth.
Shout as I may about how unnecessary it is to deploy policies to turn it off, I've already seen ridiculous things being discussed on LinkedIn/X/BSky.
The fact is, if a bad actor is not only able to get policies deployed, then separately convince a user to enable it on their device, leave it running for long enough, and then convince that user to scan their face to be able to trawl through that data... You've got FAR bigger problems in your environment.
Additionally, have a think whether you've got similar security concerns about user's existing ability to just screenshot stuff. Sure, Recall is automatically doing it, but if you're concerned I'm sure you've got a strong policy for things like Endpoint DLP and Insider Risk Management, right?! And you don't have any "employee monitoring" apps leaking sensitive screenshots in the open?
Features like Recall and M365 Copilot can be massively beneficial to people who are able to use them and incorporate them into their daily workflows. They can also be valuable accessibility tools to people with disabilities, so try and reframe personal opinions about them before leaping to decisions.
And if you're not going to be buying any Copilot+ PC's, then the entire point is moot anyway, and you don't have to do anything.
I've thoroughly enjoyed my time testing Recall, and I'll continue to try and counter the negativity against it.
Share this article: